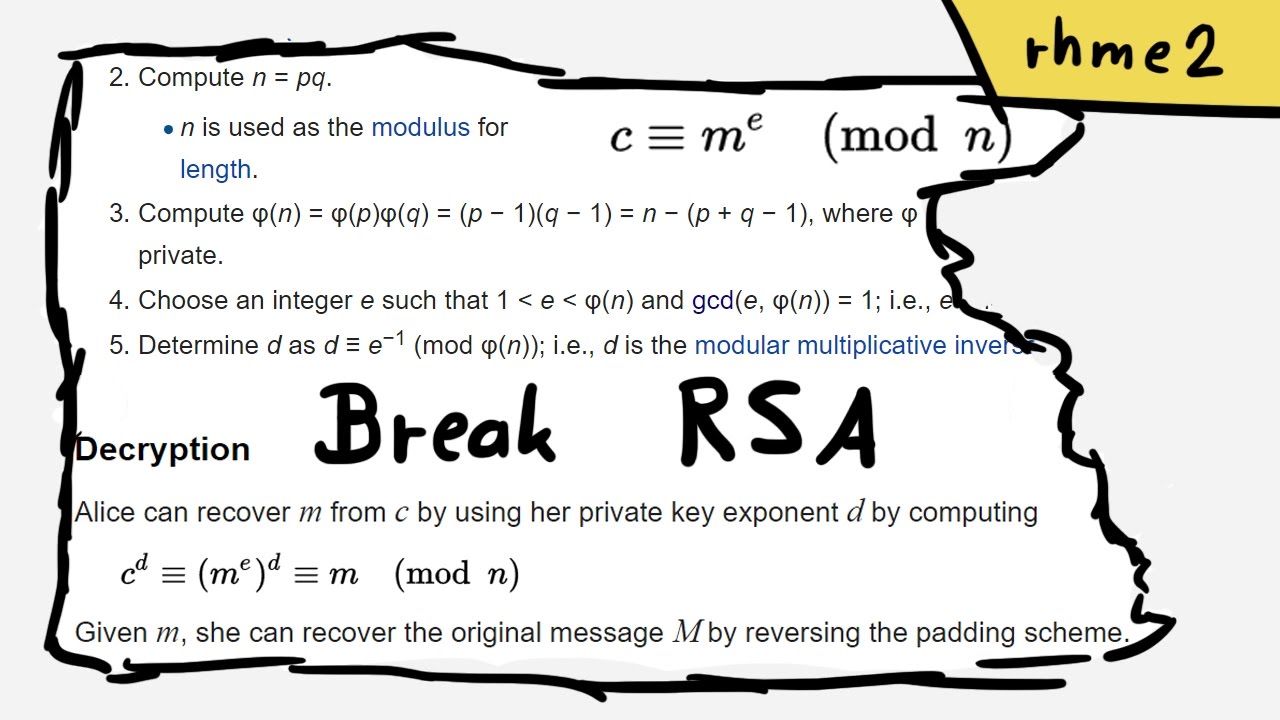
How to Remove Single Points of Failure by Using a High-Availability Partition Group in Your AWS CloudHSM Environment | AWS Security Blog

Symmetry | Free Full-Text | Homomorphic Comparison for Point Numbers with User-Controllable Precision and Its Applications

A Lightweight Proxy Re-Encryption Approach with Certificate-Based and Incremental Cryptography for Fog-Enabled E-Healthcare

PDF) Prediction of Multi-Scale Socioeconomic Parameters from Long-Term Nighttime Lights Satellite Data Using Decision Tree Regression: A Case Study of Chongqing, China

Cryptanalysis of the Randomized Version of a Lattice-Based Signature Scheme from PKC'08 | SpringerLink
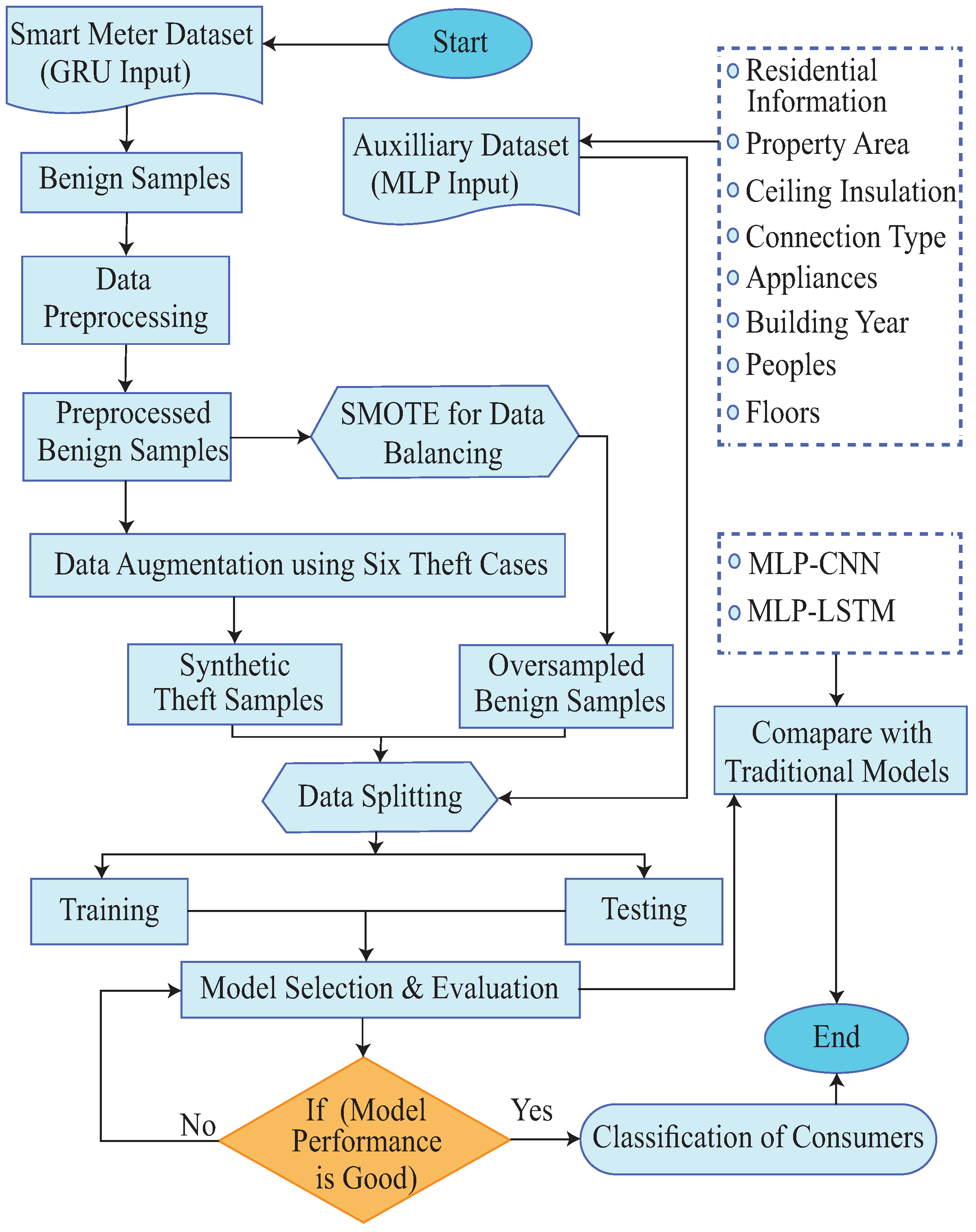
Sustainability | Free Full-Text | Detecting Nontechnical Losses in Smart Meters Using a MLP-GRU Deep Model and Augmenting Data via Theft Attacks

CTJV801 A Practical Public Key Encryption Scheme Based On Learning Parity With Noise | PDF | Cryptography | Key (Cryptography)

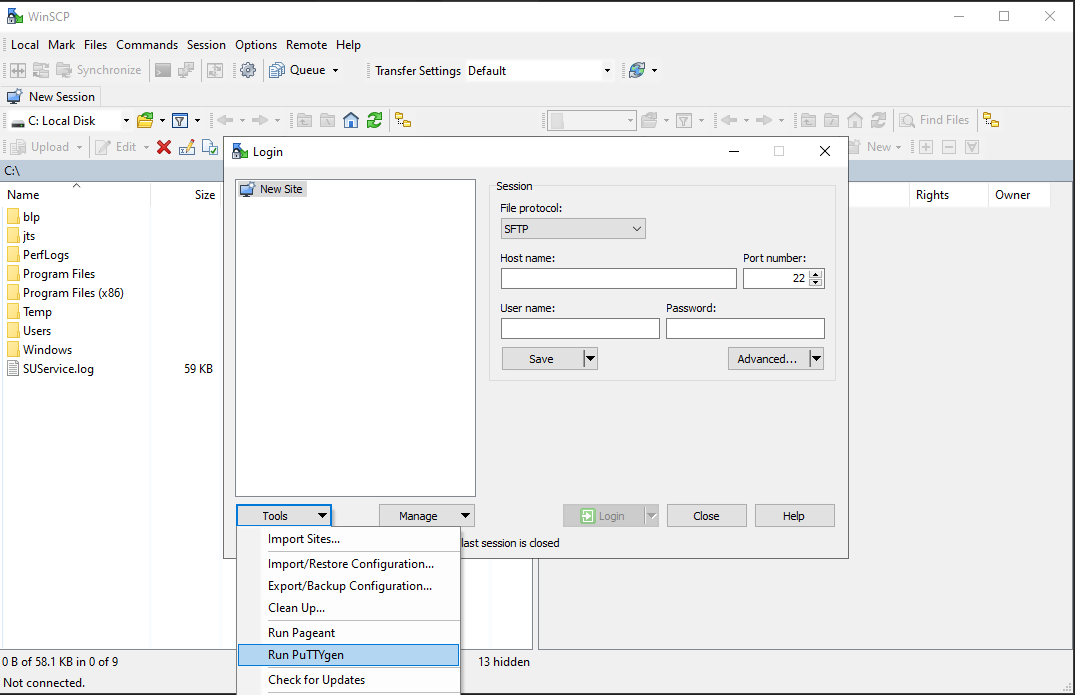









.png)